
Why we let Web 2.0 become the modern-day Stasi
''I know where everyone in this room has been the past year", Bram Bonné, a Flemish PhD student in computer science, tells the people present at his TEDx – talk. In his talk, he demonstrates effectively how the technical qualities of smartphones and Web 2.0 violate our privacy. Bonné continues by saying that one of the people in the audience has been to Bangkok, and they must be an important person as they stayed in the Hilton hotel there and also went to the Arctic. "Your smartphone is sending out information to everyone who cares to listen, as it is looking for a network. Everyone with Wi-Fi connection can access this data and modify it by pretending to be a network", he explains. "Your privacy might be more important than you think yourself."
People living in the German Democratic Republic (East Germany) must have been relieved when the Stasi was formally disbanded in February 1990, as the era of mass surveillance was thought to be over. In East Germany, under the communist regime, the Stasi (German Ministry for State Security) infiltrated every institution and every aspect of daily life between 1950 and 1989, including personal relationships. Stasi also deployed "a vast network of informants and unofficial collaborators, who spied on denounced colleagues, friends, and neighbours and even family members" (Cameron, 1998).
This article contemplates how our "culture of connectivity", as van Dijck calls it, brings forth privacy issues reminding us of Stasi-Germany, and how we all contribute to this culture. As citizens are being nudged into sharing, this results in a revival of the era of mass surveillance. With the advent of Web 2.0, shortly after the turn of the millenium, we have traded our privacy for convenience to a point of no return. And the consequences for our privacy might be more profound than many might realize.
The consequences of convenience and unawareness
Despite the internet being considered "an anonymous space", it is far from it, considering how much of our data is gathered, for example through cookie software (Skok, 2000). Nearly every activity online is reported and profiled. This has changed how we understand privacy, and what we find "necessary to ensure [our] dignity and autonomy as human beings" (Woo, 2006, p. 950).
Surrendering our data often comes down to a personal decision, but we often do not have a choice. Websites are usually built in a way that ensures that they are only useful when people agree to their data being used or when personal information is actively given. We now rely on the internet for official business too, as governments have digitalized many institutional functions such as correspondence with governmental institutions and access to our bank accounts. In fact, cookie technology-based profiling is regared by many as a valuable step forward in facilitating our lives (Woo, 2006).
However, survey-based studies show that people harbor online privacy concerns, but many seem to overcome them and become eager to surrender their data if there is something to be gained (Woo, 2006). When we log into a public network when having a drink in a bar, or when we use the Wi-Fi at the airport when traveling, we aren’t always aware that companies pick up the massive amounts of data we unconsciously disseminate by simply going online.
Yes, it is convenient to have free Wi-Fi when we’re on the road, but we actually pay for it with our data, which makes us easy targets for personalised advertising. As Woo (2006, p. 956) stresses,"in contemporary capitalist society, consumers voluntarily subject themselves to surveillance in order not to be excluded from practical benefits". This relies on the idea that we hate being excluded when there is something to be had. Already some 20 years ago, Whitaker (1999) spoke of "a ‘participatory panopticon’: a consumer panopticon based on positive benefits where the worst sanction is exclusion from these benefits."
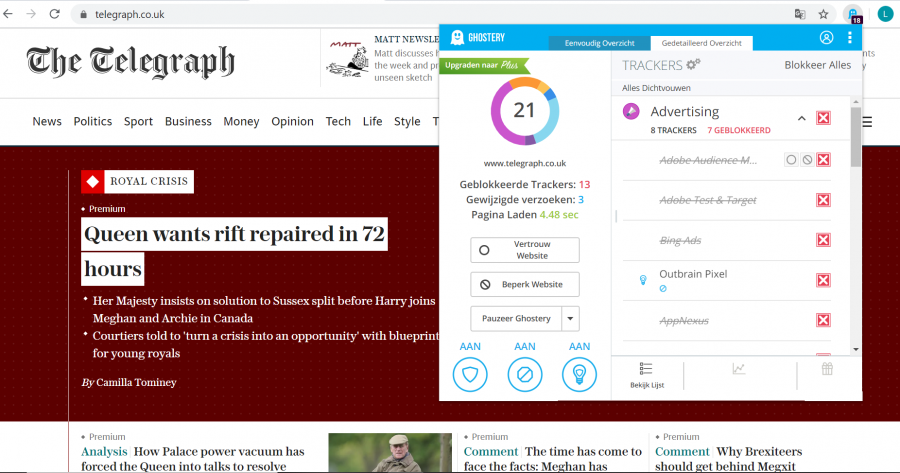
Figure 1. Even when reading a newspaper online, we are not alone. Only on this page, there are thirteen trackers present that gather our personal data and share it with platforms that benefit from it.
Data mining as a symptom of inequality
According to van Dijck (2013, p. 5), "the transformation from networked communication to platformed sociality, and from a participatory culture to a culture of connectivity, took place within a decade". New services offered by Web 2.0 were perceived as a new global infrastructure. That is, the internet as a medium evolved alongside our everyday practices, and it thus contributed to (re)shaping them (van Dijck, 2013). In the end, the ways in which we maintain contact with others through the new infrastructure's mediation have become intrinsic to the workings of our society (van Dijck, 2013). At the same time, the big platforms that have become a profound part of our daily life are designed to have us sharing as much as possible. When Facebook's Mark Zuckerberg promised to make the world "more open and transparent" - a very common slogan for corporations behind big platforms, according to van Dijck - the promise was one-sided.
The inequality of power distribution on the internet today becomes clear when one notices how we fully depend on it while there is no transparency as to how our data is treated.
Just like the citizens of East Germany were required to share information about fellow citizens to the point where one could not trust one’s own colleagues, friends or even family members, today we share information on our friends and family because we are told this makes us "more social". Being "social" on platforms, however, is ambiguous as it involves "both the sharing we do with friends and family, and the platforms’ sharing of our data with third parties for financial gain" (van Dijck, 2013).
This sharing is ideological, just like in the times of the Stasi, but it relates to another authority. Whereas the ideology of sharing in East Germany stemmed from the Cold-War communist regime trying to prevent ‘unwanted’ counter-ideologies popping up, the ideology of sharing nowadays has a commercial cause. "Surveillance, spying, marketing and advertising all means the same nowadays; zero privacy for us and data–profits for them. The surveillance possibilities afforded by today’s communication technologies are beyond a Stasi–general’s wildest dreams" (Garton Ash, 2016, p. 283). However tight the Stasi surveillance network might have been, it was not nearly as tight as our current surveillance systems are now. Mammoth corporations like Google and Facebook not only collect "terrifyingly detailed" information on us, but this data is nade extremely easy to data-mine by design (Garton Ash, 2016). Both private stakeholders and governments can then have their share of our information (Garton Ash, 2016).
The inequality of power distribution on the internet today becomes clear when one notices how we fully depend on it while there is no transparency as to how our data is treated. Cookie software, platforms’ protocols and the ideology of sharing allow corporations like Facebook to collect our data and use it to drive traffic and make a profit in ways we are not aware of (van Dijck, 2013).

Figure 2. We might not pay for everything we do on the internet with money, but we pay with our personal information, which is then converted into money by the platforms we use.
What it comes down to is that we depend on the internet as a digitalised society, and big platforms in turn find various ways to monetize our data. With their cookie software, algorithms, targeted advertising and data-profiling, platforms are the ones in charge and we are the ones depending on them like the citizens in East Germany depended on their government. When knowledge is power and data is knowledge, and when data leads to both money and power, it all comes down to inequality.
"Contemporary methods of power are methods whose ‘operation is not ensured by right, but by technique, not by law, but by normalisation, and not by punishment, but by control" (Foucault, 1980, p. 89). This quote from Foucault aligns perfectly with the kind of "online power" we are discussing. One thing that could curtail this power imbalance is network anonymity (Woo, 2006), but platforms respond to this by nudging us into sharing as much identifiable information about ourselves as possible.
Social consequences of online privacy violations
In the early days of Web 2.0, the situation regarding personalized ads and personal data being shared was a lot different. As new features came along, users started to accept the new norms that emerged with them (van Dijck, 2013). At this point, just as people in Eastern European countries became used to on-going privacy violation and had no choice but to accept that the Stasi would know as much as possible about them, we as contemporary citizens appear to have no choice but to accept that our data is shared.
The persistent problem with privacy nowadays however, is not so much that we don’t have it as much as we should, but instead, that a small group of people has control over our data.
The meaning of privacy is contextual: it varies historically and across different people and groups of people (Garton Ash, 2016). For example, some cultures today may understand privacy as a concept a lot differently than ancient cultures, or other present-day cultures in different parts of the world. The persistent problem with privacy nowadays however, is not so much that we don’t have it as much as we should, but instead, that a small group of people has control over our data. Problems can arise as a result of our constant sharing of information, for example, when we lose a job opportunity because a manager found our drunk "nightlife photos" online, or when we miss important emails because they have become indistinguishable from targeted advertising emails.
Privacy International, a charity that challenges governments and companies that want to know everything about individuals, describes privacy as "the right to control who knows what about you and under what conditions" (Garton Ash, 2016, p. 289). Needless to say, on the internet, we don’t know who knows what about us and under what conditions. An important change in privacy dynamics with the advent of Web 2.0 came with the fact that "the ‘privacy invading entities’ have become broader but less identifiable" (Woo, 2006, p. 954). Technicological developments have widened the gap between information "haves" and "have nots". "The privacy divide", as Woo calls it, is "the gap between users’ level of consciousness regarding online privacy. This difference may result in a serious gap in the degree of empowerment and self-employment" (Woo, 2006, p. 957).
Run by Erich Mielke, a veteran communist, the Stasi was one of the most feared and effective secret police forces in history. "It recorded conversations, opinions, medical histories and any contact with foreigners, in millions of carefully numbered and classified files; the Stasi files", Adam Lebor tells the Guardian. It is funny in a strange way to notice that this recording and filing of the Stasi is not so different from the contemporary data mining done by Google, who in fact gains most of its staggering wealth by selling the data it gathers from us to third parties (Garton Ash, 2016). Although "anonymized", the data about us that Google classifies is so much that we become identifiable from our data profiles.
We should be aware that when we are online, we are not alone. Also, the internet doesn’t forget; anything we share online is like a tattoo (Garton Ash, 2016 p.290). Garton Ash (2016 p. 285) describes privacy as ‘the ability to choose what you want to keep private and then to have confidence that this choice will be respected’. Talking about being aware of this, Garton Ash says: ‘’I think back to Eastern European dissident friends in their kitchen, writing down cryptic messages on scraps of paper to avoid the listening microphones of the secret police.’’ (Garton Ash, 2016 p.285)
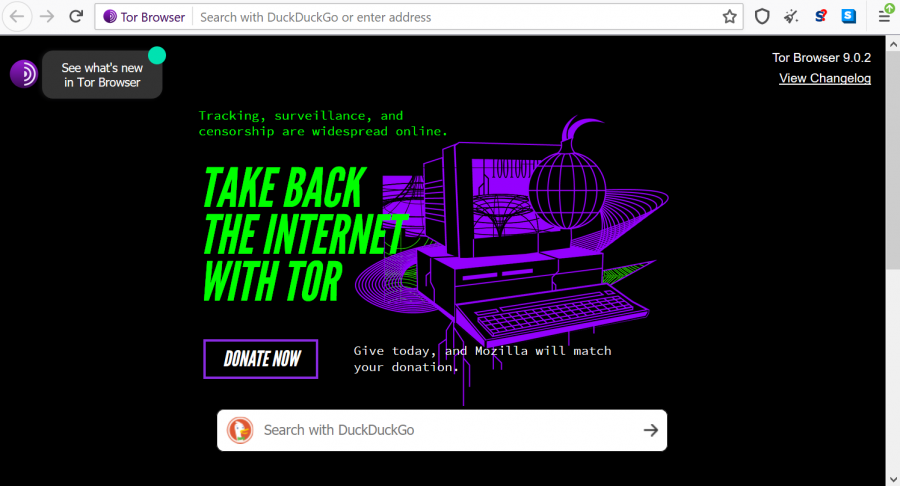
Figure 3. Tor: a privacy-friendly browser on which cookie softwares do not function.
From the Stasi to surveillance capitalism
A lot has changed since the fall of the Berlin Wall. Modernism and Fordism were replaced by post-modernism and superdiversity, communist regimes lost territory and the internet has now become our main infrastructure for communication. What did not change much, however, is the way in which our privacy is still being violated by tose in power. Whether it is a communist dictator or a small elite of internet platforms in charge, we are still being watched, followed, classified and targeted on an enormous scale. We are simply less aware of it.
In networked environments, one submits to this power imbalance since users don’t have a practical option not to provide personal information and, on top of that, they are mostly unaware of just how much information they are providing. Further, as van Dijck (2013) notes, "the ideology of sharing has become embedded in our contemporary culture" and it benefits incorporations and governments, consolidating their power further. We essentially become the product by (unknowingly) sharing our data and thereby paying for services with our privacy. Adam Lebor states in The Guardian "how wonderful it is that the era of intrusive mass surveillance is over", but, upon further examination, we realize this is not the case at all.
If we don’t want to be tracked by companies, we have to take active measures to protect our online privacy. This can be achieved by making simple changes, for example by using an ad blocker on our browsers or by using the privacy-friendly Tor browser. We should also learn how to use the privacy settings on our phones and our social media, and remember that everything we share online is not only being shared with our friends on Facebook.
In the end, besides taking whatever small precautions we can, it is most important that we become aware of (and come to grips with) the fact that the invasion of our privacy is inherently connected to the contemporary techno-economic system of surveillance capitalism. Small patches and fixes will not change that system.
References
Cameron, J. (1998, July 20). Stasi - East German Government. Enceclopaedica Britannica.
Van Dijck, J. (2013) The culture of connectivity: A critical history of social media. New York: Oxford University Press.
Foucault, M. (1980). An introduction. Vol 1. The History of Sexuality. New York: Vintage. P.89. Cited in: Van Dijck, J. (2013) The Culture of Connectivity: A Critical History of Social Media. New York: Oxford University Press.
Garton Ash, T. (2016) Free Speech. London: Atlantic Books.
Skok, G. (2000) ‘Establishing a Legitimate Expectation of Privacy in Clickstream Data’ , Michigan Telecommunications & Technology Law Review 6: 61-85. Cited in: Woo, J. (2006). The right not to be identified: privacy and anonymity in the interactive media environment. New Media & Society, 8(6), p.955.
Whitaker, R. (1999) The End of Privacy: How Total Surveillance is Becoming a Reality. New York: The New Press. Cited in: Woo, J. (2006). The right not to be identified: privacy and anonymity in the interactive media environment. New Media & Society, 8(6), p. 956.