
The literacy advantage of glitch text for hacking
A glitch is, simply put, a system malfunction that occurs for a brief period of time and is difficult to debug. Hackers can make use of glitch text to get into computer systems and steal, modify, or delete data, typically without your knowledge or agreement, by installing hazardous malware. By making use of Zalgo text, the digital text will be modified by combining characters and Unicode symbols to add diacritics above or below letters. The use of this glitch text has different expressions and functions. This article will draw on how glitch text is becoming more common in our digital society and will argue on the literacy advantage of glitch text for hacking. Despite the fact that glitch text is relatively harmless in itself, it contains functionalities that can have worrying consequences when used in, for example, political conflicts. How is glitch text becoming a common practice in modern digital literacies?
Expanding digital literacy with glitch text
We can realize that acquiring knowledge about how digital literacy flows can be of great contribution to contemporary life. Specifically when working or studying in the digital realms. Currently, there are four types of competencies of digital literacy: internet searching, hypertext navigation, knowledge assembly, and content evaluation. Adding to the above, Martin’s (2008) definition of digital literacy goes as follows: Digital Literacy is the awareness, attitude, and ability of individuals to appropriately use digital tools and facilities to identify, access, manage, integrate, evaluate, analyze and synthesize digital resources, construct new knowledge, create media expressions, and communicate with others, in the context of specific life situations, to enable constructive social action; and to reflect upon this process (Koltay, 2011).
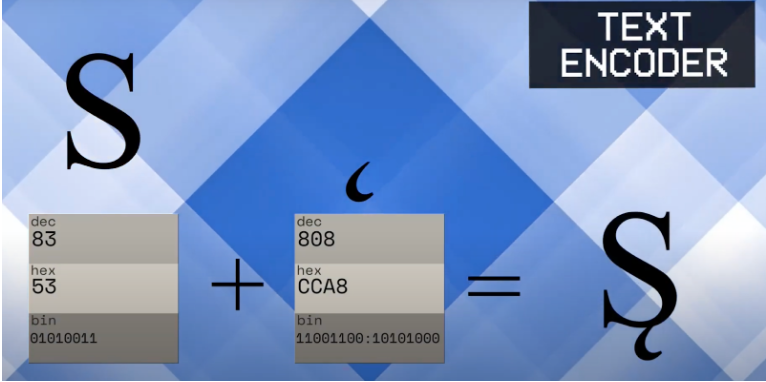
Even if these four digital literacy competencies are the requirement, there is a group of individuals with higher skills in digital literacy. This group of individuals learned a certain type of communication and skill called glitching. The base of the created glitch is found in Unicode. The Unicode Standard involves all the scripts and signs used in the world, for example, the Western script, Chinese script, and emojis. Each sign is connected with a unique code so that the computer can understand it. Currently, over 65,000 characters are defined and coded in the Unicode Standard, but new signs are added to the Unicode Standard over time (Needleman, 2000).
The Unicode Standard is important for computer systems to load and work. But when it comes to a glitch, the computer is unable to read the given code and it will be seen as an unexpected output resulting from short-term electronic or software storage (Menkman, 2011). How is the Glitch created? For example, using the letter S will have a unique binary code. By adding diacritic symbols to a letter, this letter will still occupy the same space, however, the binary code of the letter will expand making it difficult to render. The merge of these two symbols will create a new code and this code is not findable in the Unicode Standard. Individuals who practice Glitch however do not use one or two symbols to create glitches, but more than a hundred symbols are used to Glitch a system. To create a glitch, the individual needs to practice coding, which is not one of the four competencies in digital literacy and so an extra skill.
Glitch practice used to be a very rare case, but in today's era is it becoming more common. For instance, the company Coca-Cola used the Glitch practice in a recent tweet. In the tweet, they used Glitch to communicate: "Y’all got any #CocaColaStarlight". Coca-Cola's use of glitches is a simple and fun way to communicate. But this is not the only way to put Glitch into practice. The different types of ways to use Glitch are for fun and experimenting, to create art and communication, and to hack into systems. Since Glitch is becoming more common and even used by large companies to communicate, these three types of glitching will be analyzed to discover the type of skill and the meaning behind the use. The important factor here is to see if the current digital literacy competencies should be expanded to adding learning coding since the use of glitch text is getting more common. The top-down vs bottom-up processing will be used to analyze this case.
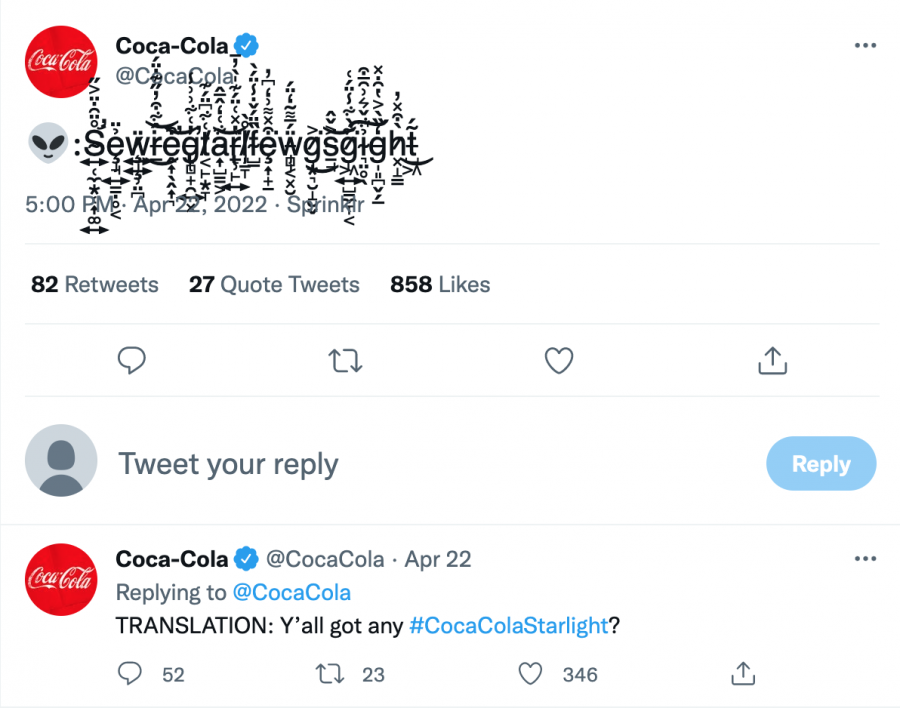
What happens when literacy reaches a range of people for different purposes? In this analysis, there are four types of investigating practices in the use of this Glitch text. It is seen that literacy on this topic has been spreading little by little at different times in the history of the internet. TikTok, Facebook, Twitter, Tumblr, and many other networks have hosted this type of digital practice on their platforms. In its beginnings, people began to create memes related to "Cthulhu", a cosmic deity created by the writer Howard Philips Lovecraft in 1928. These images contained a comparison of a text without error and another text with an error that is linked to Cthulhu. This is where literacy began to come to life in the common people, all through a viral image. The analysis found four different situations in which different people made use of this glitch practice. What is meant when it is referred to this practice as being part of different forms of use?

How Glitch is used by a student to explore the practice
To begin with, the first level of using glitch text will be addressed; the use of this practice is purely for fun. The TikToker Jooystin in the year 2019 made use of glitch text in his graduation yearbook. In this yearbook, all students had to hand in a senior quote via Google Forms, which could be used under their school picture. Jooystin had the idea to copy and paste the word "hamburger" with excessive diacritical marks in each letter causing a mess in the layout of the yearbook, which in turn covered Jooystin's picture and that of one of his classmates in glitch text. This caused difficulties in the visualization of both pictures. As it is seen in this case, this person simply had the curiosity to copy and paste a glitched text into a physical object, this is used as a practice merely for fun and entertainment purposes.

This case of exploring Glitch fits into the bottom-up process. The bottom-up process is driven by the exploration of the surroundings of the environment (Kinchla & Wolfe, 1979). In this situation, the individual in question is studying the features in front of come to the bigger picture. Taking a small step to come to the goal. This type of learning can be seen in the early stages of development. In the case of Jooystin, there is an interest in glitching, but no existing knowledge of how to build one by using coding. So, he is using the existing knowledge, internet searching, to build a glitch. A glitch generator is used to build the glitch he then used in the yearbook. In this case, the build of glitch can fit into the existing four competencies of digital literacy and no extra skill was used or learned.
The next level is about curiosity, in January 2018, the company We Are Segment caused the crashing of the most popular email service, Gmail. Roberto Bindi, a young hacker, came up with the idea of sending an email with glitched text to a specific address causing the user to be denied access to the messaging account. The company mentioned that what happened was merely out of curiosity. At this certain level, the use of glitch text also lies within the bottom-up process. The hacker had no further experience with this type of hacking, he was merely exploring the ways he could use this glitch to hack Gmail.
When looking at the digital literacy aspect, it goes a little further than the four competencies since it is a way of exploring how to glitch a system that eventually worked.
Creative exploration by a digital artist
The artist Laimonas Zakas also known as Glitchr has been playing with diacritics since 2011. This started when he published a glitched text in his feed which caused the Facebook layout to break, upon discovering that Facebook was not yet aware that people could do this on their platform. Glitchr was a pioneer in turning his profile into a work of digital art. Publications, the description of his profile, hyperlinks, everything was glitched in such a way that he captured the attention of the Facebook developers (at that time). Today the artist continues to intervene on web pages. Several of his performances have been exposed around the world. And the most curious thing is that the Facebook developers have sought to ask him to find errors in the Facebook system as an ethical hacker.
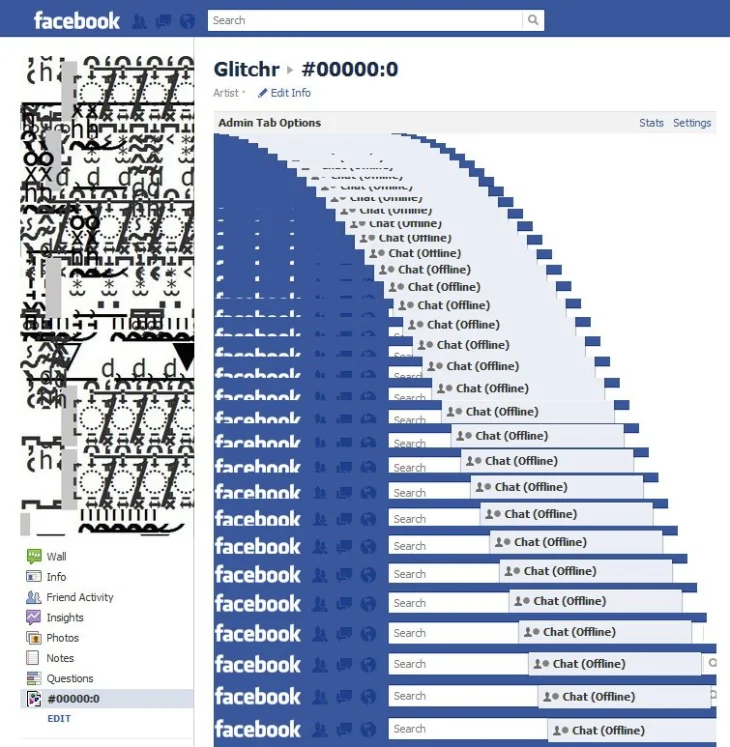
For the creation of art with Glitch, the user needs to have a certain type of knowledge of coding. From this level, the user is making use of the top-down process. This process is driven by prior knowledge and information existing in the individual’s mind (Kinchla & Wolfe, 1979). Prior knowledge is important in the decision-making process, goal, or the bigger picture of what is in front of the individual. The exploration of the surroundings or environment comes later in the process. Prior knowledge in this process is the most important aspect. If the creator in question wants to make art with Glitch, the knowledge of coding must already be present. So, the knowledge of coding in this process is more important than how the art is eventually going to look. Without coding knowledge, art cannot be created as that is wished for. The skill of coding and creating art with it, are two skills that are higher than the basic required digital literacy skills. In this case, the creator owns a larger knowledge of literacy than the general public.
Security systems and political parties are facing more threats through glitch texts
The fourth level is where things get tricky. As ABN AMRO's project manager says: "technology is like a knife, it can save or take lives, but most people use it to put butter on their bread"
This practice of glitching has reached a very high stage in the world of hacking. Hackers all over the world use this practice of glitched text to bug servers and subsequently bypass security systems. This happens through something called DDoS which stands for Distributed Denial-of-Service Attack. This cyber-attack consists of flooding a server with internet traffic to prevent users from accessing services and sites connected online. In short, hackers send texts in a hyper-fast way to servers causing a slow rendering, we can say that there are a million messages sent in less than a second. This overload of information causes the breaking of the system, generating an entry to the server's security system.
For this last level, we investigated what the internet calls "Mining Secrets". We found that these types of DDoS attacks are currently being used to extract confidential information within the political conflict between Ukraine and Russia. Many of these attacks have been used to publicly disclose Russia's moves against Ukraine. Within all this information that has become public through DDoS, we could find several topics, many of these related to oil and gasoline. The 'DDoSecrets' group (DDoSecrets standing for: Distributed Denial of Secrets) seeks the "free transmission of data in the public interest" by distributing hacked and leaked data from more than 200 organizations including U.S. law enforcement agencies, offshore banking firms, and government ministries. DDoSecrets has published at least ten pieces of data that hackers allegedly obtained from Russian organizations, including the government's Internet censorship agency Roskomnadzor, the Central Bank of the Russian Federation, Rosatom State Nuclear Energy Corporation, and the All-Russian State Television and Radio Company. Among the data released by the group are hundreds of thousands of emails and internal documents.
In this last level, a high set of digital literacy is required. Also, this process of using Glitch fits into the top-down process. In this process, the hacker already has knowledge of both using glitching, coding, and hacking. What is interesting about this set of knowledge, is that the person in question acquired knowledge that is non-existent within the system. It can go so far that the system has to update its existing knowledge to the knowledge of the hacker. For example, changing cyber-security and rules surrounding security. This could even change the digital literacy requirements for the general public as certain ways of navigating online change, due to hackers.
Glitching in modern society
The digital literacy field is expanding, and the simple four competencies seem not to be enough anymore. Since digital tools, fields, and usage are developing, it can be questioned if newer types of digital literacy should be taught to the general public. In the analyses, it is seen that the usage of Glitch is getting more common. Even when there is a big gap between the different types of usage of Glitch, newer digital literacy skills are needed when using this practice. In some cases, it even may seem that learning these newer skills should be a requirement. Especially when it comes to doing harm with Glitch such as hacking a whole governmental system. These certain attacks can even change a whole system to prevent possible attacks in the future. Since all this development and newer technology is already presently happening, why is the current type of digital literacies not updated? There is a difference in the learning type of knowledge when it comes to coding. The hackers using coding languages are having a very high set of digital literacy skills, but it should at least be considered for the general public to learn these types of newer digital literacy skills such as coding. When it comes to the current bottom-up process, these individuals are curious about the field in front of them and explore it on their own terms. If individuals learn the basic set of coding, they can make their own decision in practicing Glitch and even expand their knowledge to a top-down process. These newer types of skills should be considered to expand the field of digital literacy considering the field of technology is expanding and getting more common in use.
With this work, we would like to keep an open door to the investigation of these subjects. We believe that it is important to understand what happens in contemporary life within the cybernetic world. We cannot let this kind of situation go unnoticed because in the future we could be involved. These practices could be for fun but there is still a lot of depth within this topic.
References and Notes
Martin, A. (2008). Digital Literacy and the “Digital Society”. In C. Lankshear, & M. Knobel (Eds.), Digital Literacies: Concepts, Policies, and Practices (pp. 151-176). New York: Peter Lang.
Needleman, M. (2000). The Unicode Standard. Serials Review, 26(2), 51–54.
Menkman, R. (2011). The Glitch Moment(um). Institute of Network Cultures.
Distributed Denial of Secrets is Spreading Stolen Russian Data. (2022). Bloomberg.