
Tinder privacy is not going to happen
Tinder is the most widely used dating platform. At the same time, it remains extremely unsafe. The app has managed to collect millions of users and billions of swipes daily despite its disturbing lack of privacy. But what are the multiple ways in which Tinder fails to secure individuals' data, and why are users still willing to take the risk to keep swiping?
Millions of people struggle to find love offline. People are busy with work, school, stress, and lack of time, so a practical solution comes to mind: why not download a matchmaking app that does the searching for you? Looking for a new partner, users become especially vulnerable and are tempted to give away sensitive information. This article will try to find an answer to the question of how Tinder, the world’s #1 dating app, operates in terms of privacy and security. To do so, I will discuss existing research and analyze the platform and its affordances.
Tinder - the world’s most famous matchmaking platform
Tinder is a platform inspired by "classic" dating websites. Its innovation was to adjust an old principle of matchmaking based on sympathy to new affordances provided by smartphones. As such, Tinder is an example of how digitalization has influenced the culture of dating.
“Lovers’ capacity to connect over distance has increased drastically with the proliferation of digital media. This augmented capacity to build constant connection with a distant other has become an important condition of romantic relationship in our time.” (Su, 2016)
Tinder provided simple user experience and made matching fully automatic. The logic of the app can be described as follows: if you like the person on your screen, you swipe right and hope for a "match" to be able to start chatting with the other person; if you don’t like them, you swipe left and never see them again.
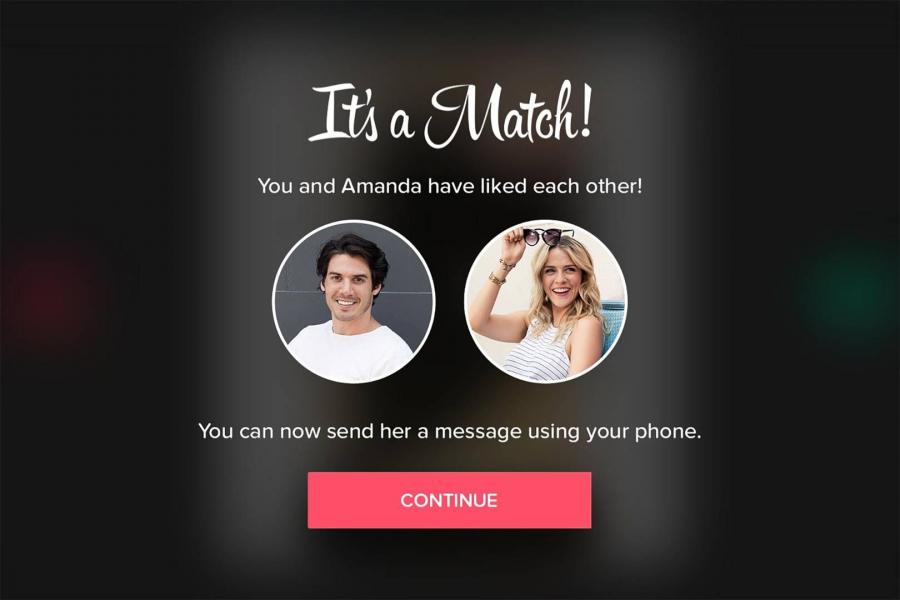
Figure 1: Tinder interface.
This clear and easy-to-pick-up matching mechanism became a success among users around the world. The new concept of choosing a potential partner made Tinder number one in the market of matchmaking apps. Tinder operates in around forty languages and is available in 196 different countries. As of 2019, the platform gets over two billion views per day, and over a million new matches per week (Tinder, 2019).
However, while focusing on user attraction and management, Tinder's security and privacy services remained quite basic compared to many other platforms. While other competing matchmaking apps such as Bumble or Happn keep updating their security services, it could be said that Tinder is moving towards simplifying them. Below, the security and privacy of the platform will be analyzed in more detail.
Tinder: Getting started
If the user wants to create an account on Tinder, the app requests an email address and phone number. The procedure is rather simple; before, it was mandatory to connect one’s Tinder profile to a Facebook account, but this function is now optional. Adding one’s Facebook page is only partly a guarantee for the verification of a user; however, it reduces the number of fake accounts, among which could be catfishing, impersonating, and scamming ones.
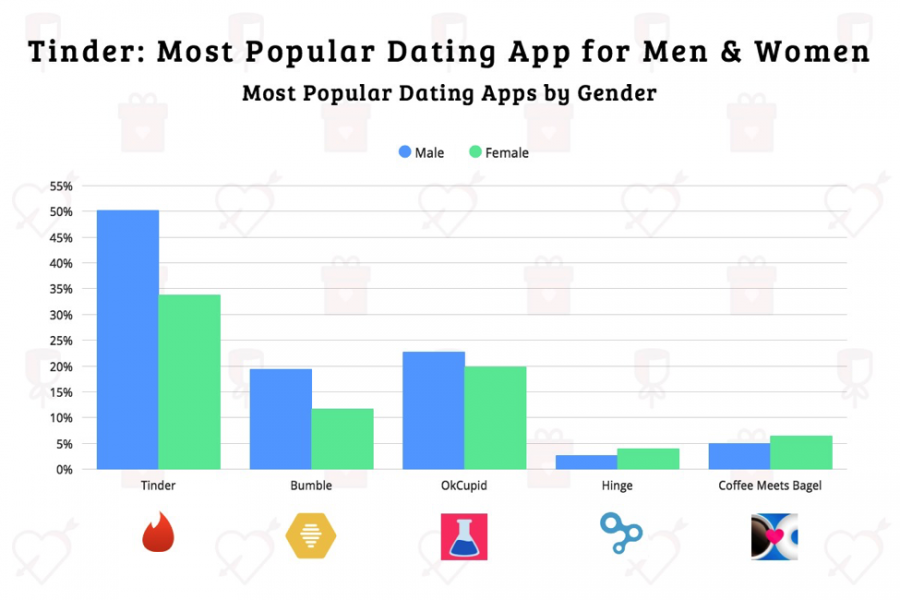
Figure 2: Tinder is the most used dating platform for both men and women.
The app also does not require a password. In case something happens to a user's account such as getting hacked or banned, one has no other option but to wait for an email from the support team of the platform. Thus, if the user loses access to their account with all their personal details, chances are high that the user will not be able to reach the profile anymore or claim verification. While waiting for the support team to email back, the user is stuck with having no access, no response, and no control over the account.
User verification is also absent on Tinder. The app does not check if the profile picture really matches with the person in control of the account. Tinder has a flourishing amount of bots and fake profiles that exploit others’ pictures for scamming, "fun", or other personal purposes. However, user verification on a matchmaking platform, in theory, should be essential as a basis for providing a secure experience.
Other matchmaking apps like Bumble already made a step towards verifying their users. The procedure is usually quite simple: the individual needs to take a picture in a certain randomly selected pose and then this photo is compared by the Bumble team member to the information presented in the profile (Bumble, 2019). If the user is unable to do so, the account will be deleted in 24 hours. Tinder, the world’s most used platform, has not tried to implement this step yet. It is rather unethical of the creators to ignore such simple steps for their users’ security. In this situation, Tinder appears to be primarily a technology to collect data for financial purposes.
How to set up a Tinder profile
Apart from being one of the most popular lifestyle apps that still lacks user protection, Tinder collects quite a lot of sensitive information about its users. “While privacy is often conceptualized as restricting access to information, participating in social media requires people to share. To exist online, people must type themselves into being.” (Marwick & boyd, 2014)
During the registration, you are required to mention your name and age, to upload pictures, and to turn on your location. From the very beginning you are required to give away valuable personal information. This gives rise to potential dangers in terms of privacy and “as Snowden revelations show, facial images (body) or location data (territory) are often collapsed into a more bland general category of information relating to persons or groups” (Lyon, 2015). The data is then grouped and categorized with no guarantee of accuracy or privacy. Besides that, the user also needs to specify whether (s)he is interested in men or women.
After setting up a profile, your personal information is visible to everyone using the platform. This might be quite problematic from the point of view of privacy because “[k]eeping in mind that privacy is about a sense of control, the notion of whether or not some content is 'public' or 'private' often misses the point. If people don't expect it, publicizing public content takes away their sense of control” (boyd, 2010). In line with this point, it is important to specify that the user on Tinder does not have any information or control over who is viewing, screenshotting, and sharing his/her profile.
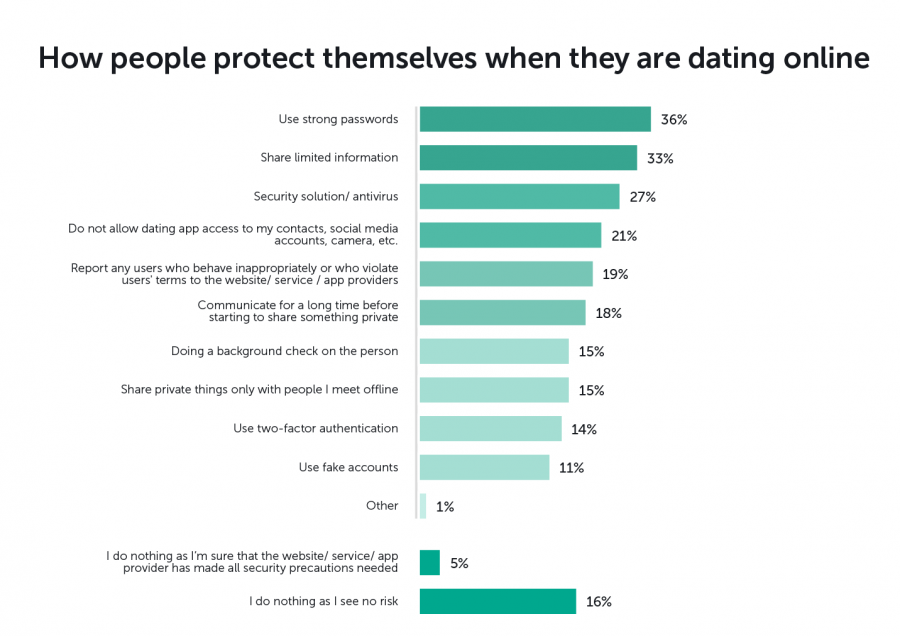
Figure 3: How people protect themselves in online dating.
The only settings that one can adjust are the age and location of the potential matches, which does not cover the need for controlling who can view your data. Entering the platform, users have certain assumptions on who might see their information. In other words, “[w]hen people interact online, they too have certain expectations and probability calculations. They make guesses about who may or may not stumble across them” (boyd, 2010).
Tinder users also have certain expectations and assumptions when they register on the platform—it's the option of doing something about it through privacy settings that's missing. No user is actually in control of who might see his/her information. This increases the chances of context collapse within the platform and makes the profile unmanageable in terms of viewers. Context collapse refers to the process "in which seemingly disparate audiences co-exist, often creat[ing] a sense of lost privacy" (Marwick, boyd, 2014).
Users of any platform usually try to calculate who is going to see the information they share and “[they] are completely reasonable, as it's an efficient way of getting a decent handle on the social context, even if they are sometimes wrong” (boyd, 2010). However, on Tinder, the chances of bumping into your boss, colleague, or ex are quite high, which is contextually rather inappropriate.
Tinder and Big Data
Tinder is developed perfectly to collect users’ data. According to Purvis (2017), in terms of psychological conditioning, the app is constructed to stimulate swiping. The purpose of the platform is to find out who swiped right for you like you did for them. This activity results in a "match", which is supported by the visual effect of a pop-up window, as demonstrated in Figure 1.
“Since users don’t know which swipe will bring the “reward” of a match, Tinder uses a variable ratio reward schedule, which means that potential matches will be randomly dispersed” (Purvis, 2017). Such a reward system is also used in slot machines, video games, and during some animal experiments (Purvis, 2017). The user feels the pleasure of having done the "right" swipe, which resulted in the "reward" of a match, and keeps on swiping to get more psychological satisfaction.
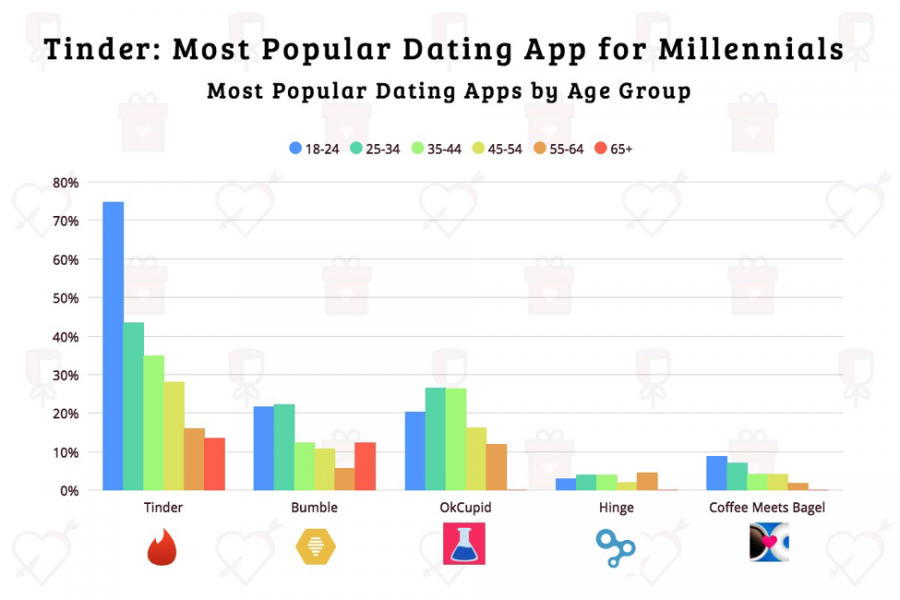
Figure 4: Tinder is the most used dating app in all age categories.
The platform does not guarantee any security of users’ personal data. Tinder’s privacy policy states that the information may be collected to deliver targeted advertising. The data collected by the platform involve all the messages, swipes, behavioral patterns, and chats by the users. Tinder is constructed in a way that allows collecting significant amounts of data on personal preferences of users. The app has access to all the data on whom one finds attractive or unattractive, as well as “how often you connect and at which times; the percentage of white men, black men, Asian men you have matched; which kinds of people are interested in you; which words you use the most; how much time people spend on your picture before swiping you, and so on” (Acquisti, et al., 2015).
The platform does not guarantee any security of users’ personal data.
If the data is hacked or stolen, your deepest dating secrets might easily be revealed to a number of people. The same might happen if the data are simply sold to any private or public company for advertising. “Tinder’s privacy policy clearly states: "you should not expect that your personal information, chats, or other communications will always remain secure [...] Tinder is often compared to a bar full of singles, but it’s more like a bar full of single people chosen for me while studying my behaviour, reading my diary and with new people constantly selected based on my live reactions.” (Duportail, 2017)
The panopticon is a concept that describes a specific system of control. It is constructed in a way which allows the "watchman" to observe everyone in the institution without them being able to tell when exactly they are being watched. Such a structure is believed to motivate the observed to adjust their behaviour accordingly. According to Jones (2017), the interpretation of Bentham’s concept of the panopticon is very influential, as it is “ an architectural structure which, through its emplacement of walls, windows, and a central observation tower, creates the conditions by which prisoners are made visible to guards, but guards are made invisible to prisoners” (Jones, 2017). Tinder becomes a variation of a panopticon that tracks and collects information that might signify one’s abnormality. In theory, privacy thus becomes “everyone’s problem” even though “profiles created from such data gathering are often misleading, irrelevant and damaging to specific individuals” (Lyon, 2015). The largest difference between Tinder and Foucault's understanding of the panopticon is that people don't seem to be disciplined, they do not change their behaviour. Tinder is more a "non-opticon": users are not expected to normalize their behavior—on the contrary, the app want us to be ourselves in order to datafy and market our profiles. It is this usage, that allows Tinder to scrape the surplus and monetize the data.
Figure 5: 800 pages on Tinder data.
The app can also analyse how "likable" you are. Recent scandals showed that Tinder has several gradations of users based on their looks. This is determined by the number of swipes you get from others as a user. If you are from a lower, or "unswipable" category, you will never get to see popular profiles.
Even though it has a scandalous reputation, users keep trusting Tinder. This matter partly touches upon dataism, which "presumes trust in the objectivity of quantified methods as well as in the independence and integrity of institutions deploying these methods—whether corporate platforms, government agencies, or academic researchers" (van Dijck, 2015). This trust in public institutions and organizations occurs despite their failure to support the privacy of the user, as we can see in the case of Tinder.
Error: Security not found
How secure is Tinder? “Security researchers say Tinder isn't doing enough to secure its popular dating app, putting the privacy of users at risk.” (Fowler, 2018) The platform has encryption flaws, which allow seeing whether the user swipes left or right. The app does not use “the secure HTTPS protocol to encrypt profile pictures. As a result, an attacker could intercept traffic between the user’s mobile device and the company’s servers and see not only the user’s profile picture but also all the pictures he or she reviews, as well.” (Fowler, 2018)
While the user thinks that (s)he experiences absolutely private Tinder usage, the effect of such a flaw is as if someone would constantly stare at your phone while you do your swiping. Such a security breach may have serious consequences for those who would prefer their data to remain private, especially in countries with restricted rights for women, homosexual relationships, or simply those who engage in relationships outside marriage (Fowler, 2018).
Is Tinder still a thing?
Although Tinder does not provide enough in terms of privacy and security, it still remains the most used dating app. Many users choose the platform primarily because of its popularity. If you use a different platform, you get a so-called Fear Of Missing Out knowing that you might not see as many people as you would on Tinder.
Figure 6: Countless lists of 'working' pickup lines for Tinder.
Over the course of time Tinder got the reputation of being a rather superficial platform for dating. Young people usually tend to talk about Tinder as a "hookup" app. There are a variety of texting strategies online that aim at making the transition to another platform (WhatsApp, Instagram) more smooth. The goal is always to move away from Tinder as soon as possibe. This results in countless online lists of opening lines and icebreakers (Figure 6).
Figure 7: Meme culture of Tinder: 'Expectation vs. Reality' and 'Tinder Surprise'.
The reputation and hype around Tinder became a culture of its own. Popular topics in Tinder online culture are "Expectation vs. Reality" which refers to when the picture does not match the person, "Tinder Kinder" which results from the app's one-night-stand reputation (Figure 7), seeing your ex's profile, posting a group picture which makes it impossible to recognize the profile's owner (Figure 8), and not getting a match (Figure 9).
Figure 8: Online culture of Tinder: 'Seeing your ex on Tinder' and 'posting group pictures'.
Why do people keep using Tinder?
With all the controversy around Tinder, a good question to ask would be why people still choose to share their personal information through the platform. Apart from hoping to find a partner, one of the reasons might be the attachment to “some voyeuristic fascination in looking, but, reciprocally, some exhibitionist fascination in being seen” (Koskela, 2004). “For many of us, we lose track of time in the digital space, as the experience becomes addictively pleasurable.” (Harcourt, 2015) Indeed, multiple users share a sense of satisfaction while swiping profiles and being swiped on, as it has the same pleasurable effect as, for example, winning in a slot machine.
Multiple users share a sense of satisfaction while swiping profiles and being swiped on, as it has the same pleasurable effect as, for example, winning in a slot machine.
Besides, “this new digital existence is disconcerting and unsettling, but practically unavoidable” (Harcourt, 2015) as digital spaces become increasingly significant. Tinder is the most used dating app in the world and if a user chooses to opt out, it can lead to fear of missing out and social pressure. The app has an ever-evolving culture around it which makes the platfrom more relatable and "fun".
However, wouldn’t it be more comforting for the users to get some security guarantees when they enter a matchmaking platform as significant as Tinder? The company does not invest enough in making its services more secure and providing more privacy. In the meantime, it keeps collecting and selling users’ data, and thereby increasing revenues and the net worth of the company year by year.
Tinder is an example of the disinterestedness of a platform in performing better in terms of privacy and security. With all the modern developments in technology and algorithms, it is questionable if users still need to sacrifice their privacy and safety in order to have a chance to succeed in dating life. Nowadays, this can also be done in a safer way.
Tinder users need to pay more attention to the information they share about themselves. Within the platform this issue becomes all about both what they decide to show on their profiles, as well as whom are they interacting with, and what personal information they share in chats. Users should follow simple tips such as: do not click on links sent in chats, do not share your address or exact location in messages to strangers, do not reveal your personal information, and always try to find evidence that the attractive profile picture you talk to is actually the person behind the screen. In the search for a new date, people tend to forget about security measures and are willing to open up. If Tinder fails to secure this experience, there is nothing left for users but to take control and responsibility for what they do online.
References
Acquisti, A., Brandimarte, L., Loewenstein, G. (2015). Privacy and human behavior in the age of information. Science. 347 (6221): 509-514.
boyd, d. (2010). "Privacy, Publicity, and Visibility." Microsoft Tech Fest. Redmond, March 4.
Bumble, (2019). Bumble Photo Verification - KISS CATFISH GOODBYE.
Duportail, J. (2017). I asked Tinder for my data. It sent me 800 pages of my deepest, darkest secrets.
Fowler, B. (2018). Flaws in Tinder App Put Users' Privacy at Risk, Researchers Say.
Harcourt, B. E. (2015). Exposed. Desire and disobedience in the digital age. Harvard University Press. Cambridge, Massachusetts.
Jones, R. H. (2017). Surveillant landscapes. Linguistic Landscape 3 (2): 149-186.
Koskela, H. (2004). Webcams, TV shows and mobile phones: Empowering exhibitionism. Surveillance & Society 2 (2/3): 199-215.
Marwick, A. E., boyd, d. (2014). Networked privacy: How teenagers negotiate context in social media. New Media & Society 16 (7): 1051-1067.
Purvis, J. (2017). Strategic Interference and Tinder Use: A Mixed-Method Exploration of Romantic Interactions in Contemporary Contexts. ProQuest LLC.
Su, H. (2016). Constant connection as the media condition of love: where bonds become bondage. Media, Culture & Society: 1-16.
Tinder, (2019). About Tinder.
Van Dijck, J. (2015). Datafication, dataism and dataveillance: Big Data between scientific paradigm and ideology. Surveillance & Society 12(2): 197-208.